As a Technology Management professional - I must confess I’ve been a little bit behind the curve when it comes to understanding Cryptocurrencies. To a certain extent that’s deliberate, given the hype & marketing cliches that surround any new technology , it takes a while to ascertain if the new is another gimmick or a mind bending disruption on the horizon . While the jury is still out on the efficacy of cryptocurrencies - especially the question, do they provide any value in the real world - I think it is pertinent though to understand the basics that make Blockchain, as a technology & Token Economy possible.
I realize, I’ve already mentioned some of the terms that sound geek ( or Greek & Latin if you prefer that ). In this article I discuss the basics of Cryptography & my source is the book The Basics of Bitcoin & Blockchains by Antony Lewis.
Let’s begin by understanding what’s Cryptography ?
Cryptography is all about sending secret messages that can be read only by the intended recipient. Now, when the messages are shared over the internet its’ not very difficult for eavesdroppers to snoop on the messages. More so if the information has financial implications, such as, if Alif is transferring electronic money to Behrouz - he wouldn’t want Sasha, Saha or Sahira to know the amount of money that has been transferred or may be even the information that he has transferred anything at all for that matter.
How does one achieve this over the internet or any network of computers that are interconnected?
To achieves this, a message is encrypted mathematically using software programs by the originator . Once these messages are received by the recipient these are decrypted .
In a nutshell :
Encryption is the process of turning a plaintext (i.e., readable ) human message into cyphertext, so that if the encrypted message is intercepted a snooper can’t understand it.
Decryption is the process of turning the cyphertext back into readable plaintext.
This process of encryption & decryption is Cryptography .
There are 3 main components in Cryptography:
Key Pair
Hashing
Digital Signature
Let’s look at each of these components in detail :
Key Pair
A key pair consists of two mathematically linked keys : a public key & a private key . Public key can be shared with the world & anyone can use it to encrypt messages for you. The private key is known only to you to decrypt those messages .
PGP ( Pretty Good Privacy ) is a scheme developed in the 1990’s for encrypting, decrypting and digitally signing email messages.
Bitcoin uses a different scheme called ECDSA - Elliptic Curve Digital Signature Algorithm .
Hashing
A hash function is a series of mathematical steps or algorithms that you an perform on some input data, resulting in a fingerprint, or digest, or simply, a hash .
A cryptographic hash function is special & has some characteristics that makes it useful in cryptography & for cryptocurrencies - such as ;
It is deterministic - so the same message always results in the same hash .
It’s quick to compute.
It’s not feasible to generate a message from its hash .
A small change to a message should change the hash value extensively so that the new hash value appears uncorrelated with the old hash value .
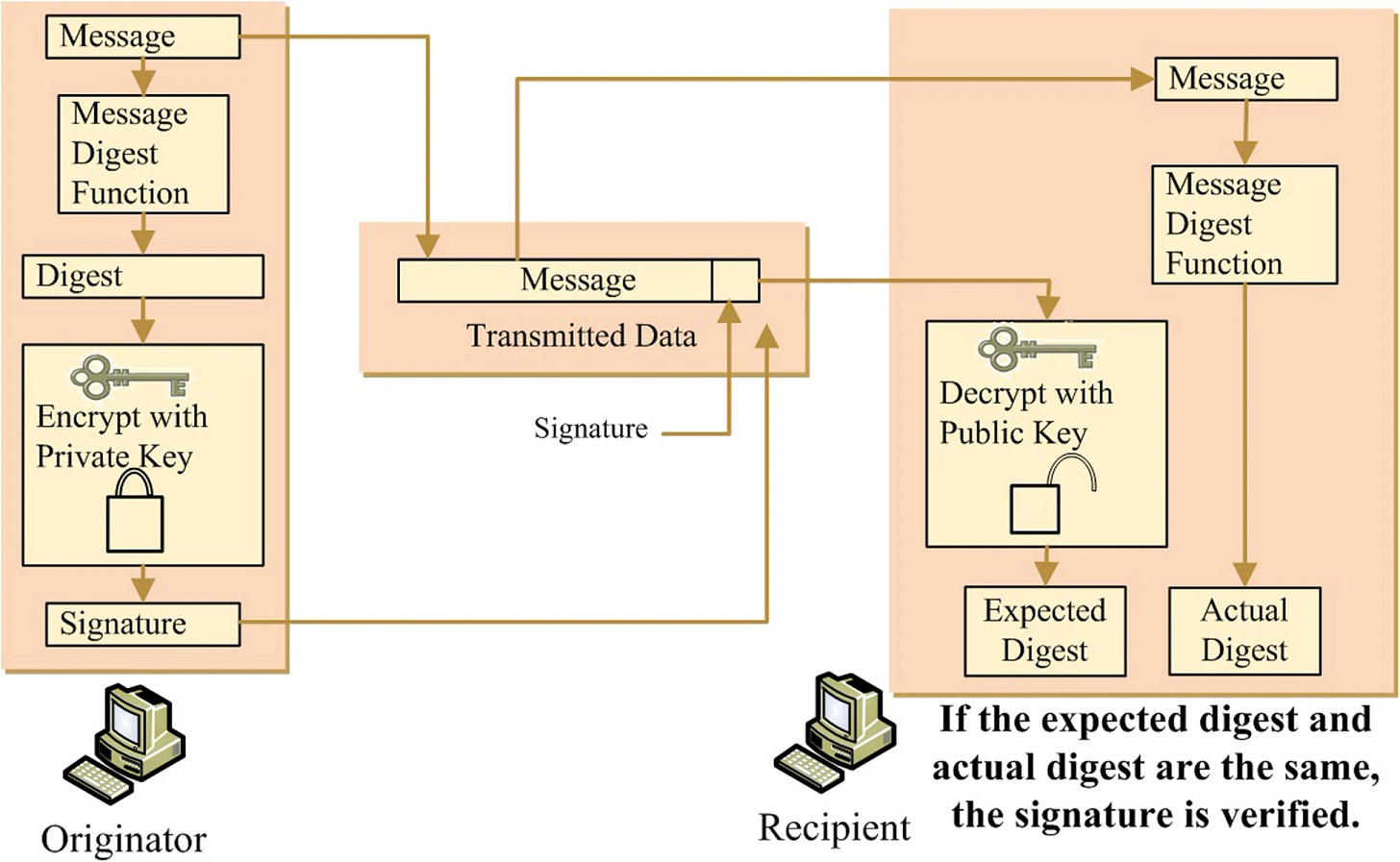
Digital Signatures
A digital signature is created by taking the message you want to sign and applying a mathematical formula with your private key . Anyone who knows your public key can mathematically verify the that this signature was indeed created by the holder of the associated private key ( but without the knowing the private key ) .
So, anyone can independently validate that this piece of data was signed by the private key holder of this public key .
Message ( Digest Function/ Hash ) + Private Key → Digital Signature
Message + Digital Signature + Public Key → Valid/ Invalid
Digital Signatures are a subset of e-signatures & are used in blockchain transactions because they prove account ownership, and the validity of a digital signature can be proven mathematically and offline, without asking any other party.
There is more to discuss on the topic of cryptocurrencies, that we shall in near future. If you have more book or research articles references to share, please post them in comments.
P.S : Antony Lewis recommends reading Steven Levy’s book Crypto to learn the in-depth story of PGP.