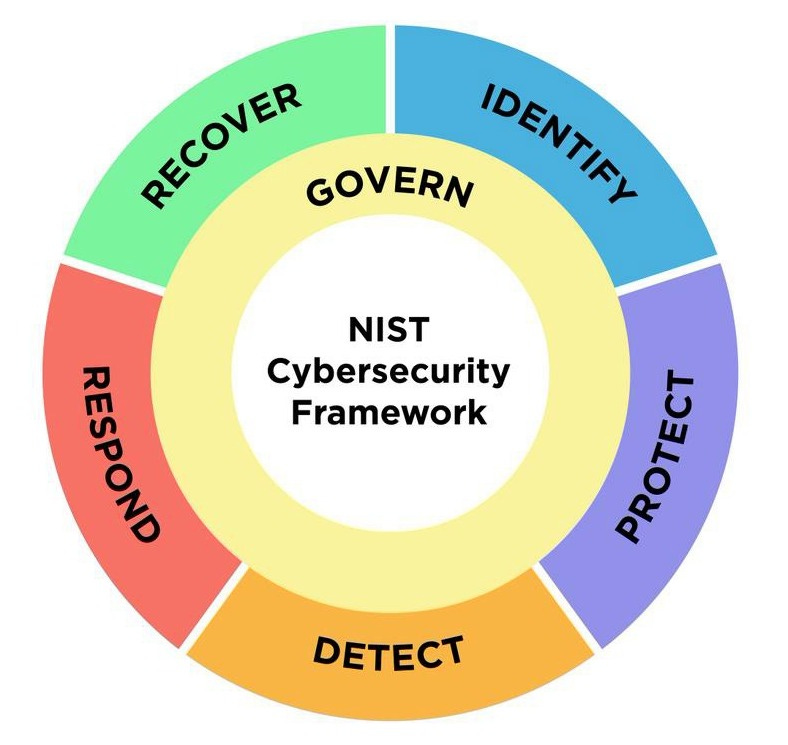
The NIST Cybersecurity Framework (CSF) 2.0, developed by the National Institute of Standards and Technology, represents an evolution in cybersecurity practices, aiming to provide a more comprehensive approach to cybersecurity risk management across all sectors, not limited to critical infrastructure. Here's a detailed explanation based on the general understanding and updates associated with CSF 2.0:
Core Functions of NIST CSF 2.0:
Identify: This function involves understanding and managing cybersecurity risks in the context of the organization's mission, assets, data, and capabilities. It includes developing an organizational understanding, risk management strategy, and conducting a risk assessment.
Protect: Focuses on developing and implementing appropriate safeguards to ensure delivery of critical infrastructure services. This includes identity management, access control, awareness and training, data security, information protection processes, and maintenance.
Detect: Enhancements in CSF 2.0 might include more detailed practices for continuous security monitoring, which involves identifying the occurrence of a cybersecurity event. This function ensures timely detection of anomalies or incidents.
Respond: This function outlines the activities an organization engages in when a cybersecurity incident is detected. CSF 2.0 could emphasize more on incident response planning, communication, analysis, and mitigation activities.
Recover: It aims at restoring any capabilities or services that were impaired due to a cybersecurity incident. This involves recovery planning, improvements, and communications.
New Elements or Enhancements in CSF 2.0:
Govern: While not explicitly mentioned in previous versions as a core function, discussions around CSF 2.0 have highlighted the importance of governance. This could include cybersecurity policies, processes, and procedures, which guide the organization's approach to managing cybersecurity risks.
Implementation Guidance: There's a noted enhancement in providing more detailed implementation examples, which separates from the core framework, allowing for regular updates without revising the entire document.
Profiles: Organizations create "Current" and "Target" Profiles to assess their cybersecurity maturity and alignment with business requirements. CSF 2.0 offers more nuanced guidance on creating these Profiles, emphasizing how they can be used to drive cybersecurity improvements.
Tiers: These help in understanding the organization's cybersecurity risk management practices' sophistication. CSF 2.0 refines how these Tiers are evaluated, possibly integrating more real-world scenarios or industry-specific nuances.
Risk-Based Approach with Emphasis on Outcomes: While maintaining its core risk-based approach, CSF 2.0 focuses more on outcomes rather than prescriptive methods, allowing organizations to innovate within their cybersecurity strategies.
Community and Organizational Profiles:
CSF 2.0 introduces or elaborates on the concept of Organizational and Community Profiles. Organizational Profiles help in aligning cybersecurity activities with organizational goals, while Community Profiles assist in sharing cybersecurity practices across similar sectors or communities, fostering a collective approach to cybersecurity.
Key Considerations:
Scalability: One of the strengths of CSF 2.0 is its scalability, applicable from small businesses to large enterprises across different sectors, which are reflected in tailored guidance or examples within the framework.
Flexibility: The framework continues to be voluntary, encouraging adaptation rather than strict compliance, which is crucial for its global acceptance and implementation.
Continuous Improvement: There's an implicit push in CSF 2.0 towards viewing cybersecurity as a continuous process, not a one-time setup, which aligns with the evolving nature of cyber threats.
The NIST CSF 2.0, through these enhancements, aims to provide a more adaptable, scalable, and actionable framework for managing cybersecurity risks, reflecting the dynamic nature of cyber threats and technological advancements. This version likely encourages organizations not only to secure their environments but also to engage in governance that promotes a culture of cybersecurity awareness and proactive risk management.
For more details visit : NIST
Created using grok .
·